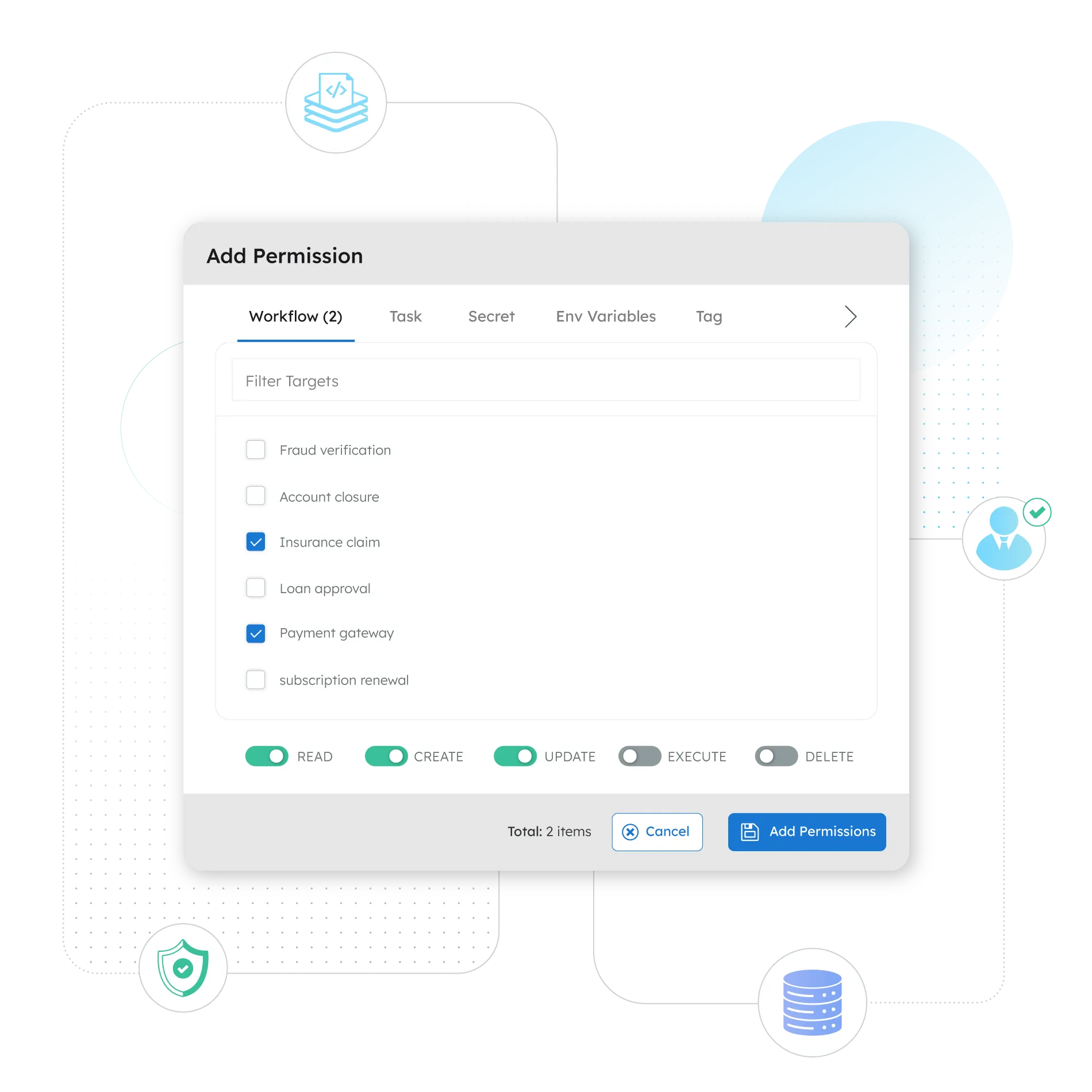
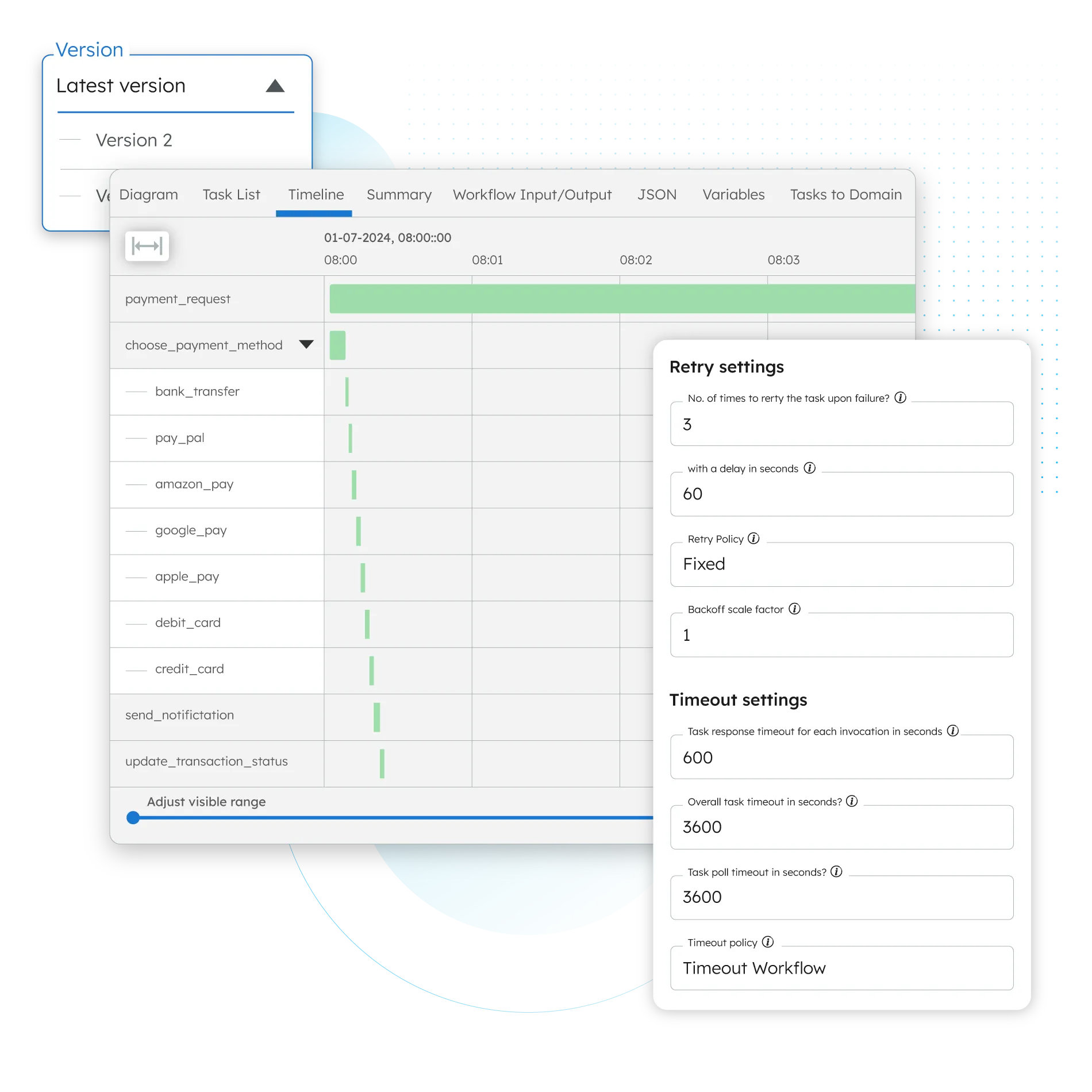
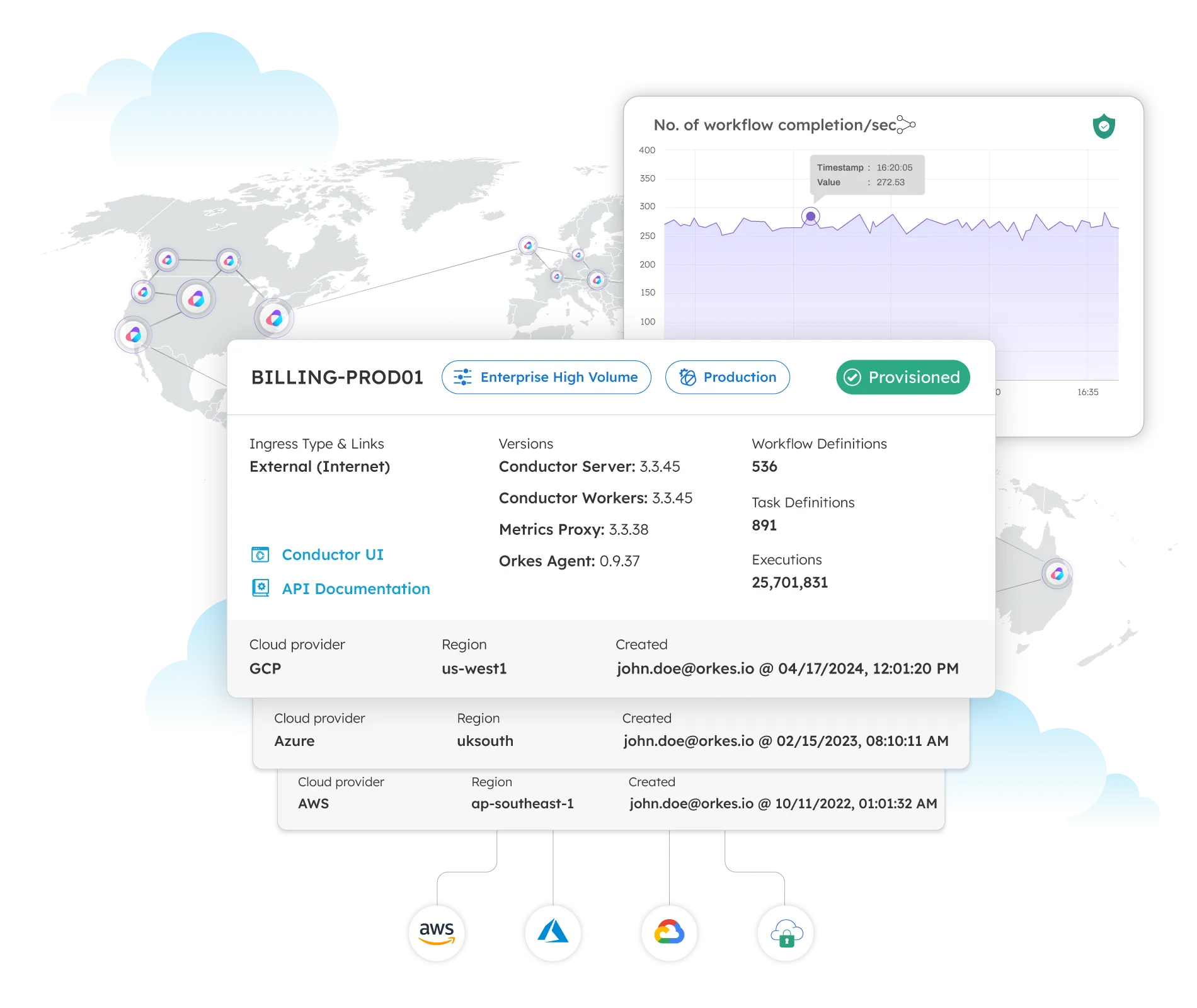
Financial Services
Secure and comprehensive workflow orchestration for financial services
Orkes’ industry leading and open source backed workflow orchestration platform provides a unified approach to distributed application development. Orkes’ battle tested suite of features ensures reliable scalability and application development velocity while increasing your security and compliance postures.