AWS SQS Integration with Orkes Conductor
To use the Event task, Event Handler, or enable Change Data Capture (CDC) in Orkes Conductor, you must integrate your Conductor cluster with the necessary message brokers. This guide explains how to integrate AWS SQS with Orkes Conductor to publish and receive messages from queues. Here’s an overview:
- Get the required credentials from AWS SQS.
- Configure a new AWS SQS integration in Orkes Conductor.
- Set access limits to the message broker to govern which applications or groups can use it.
Step 1: Get the AWS SQS credentials
To integrate AWS SQS with Orkes Conductor, retrieve one of the following credential sets from your AWS account, depending on how you choose to connect to Conductor:
- AWS account ID and region - Use this option when assuming a role from the same AWS account.
- Amazon Resource Name (ARN) and External ID - Use this option when authenticating directly with AWS access keys.
- Access key and secret from AWS account - Use this option when assuming a role from a different AWS account.
Step 2: Add an integration for AWS SQS
After obtaining the credentials, add an AWS SQS integration to your Conductor cluster.
To create an AWS SQS integration:
- Go to Integrations from the left navigation menu on your Conductor cluster.
- Select + New integration.
- In the Message Broker section, choose AWS SQS.
- Select + Add and enter the following parameters:
| Parameters | Description | Required / Optional |
|---|---|---|
| Name | A name for the integration. | Required. |
| Connection Type | The connection type, depending upon how to establish the connection. Supported values:
| Required. |
| Region | The valid AWS region where the SQS is located. For example, us-east-1. | Required. |
| Account ID | The AWS account ID. | Optional. Note: Use the Account ID if an ARN is not specified for the "Sink" in workflow definitions containing an Event task. |
| Role ARN | The Amazon Resource Name (ARN) to set up the connection in the format arn:aws:sqs:region:account-id:queue-name. | Required if Connection Type is Assume External Role. |
| External ID | The external ID that will assume the role, if applicable. External ID is used in an IAM role trust policy to designate the person who will assume the role. | Required if Connection Type is Assume External Role. |
| Access Key | The access key of the AWS account. | Required if Connection Type is Access Key/Secret. |
| Access Secret | The access secret of the AWS account. | Required if Connection Type is Access Key/Secret. |
| Description | A description of the integration. | Required. |
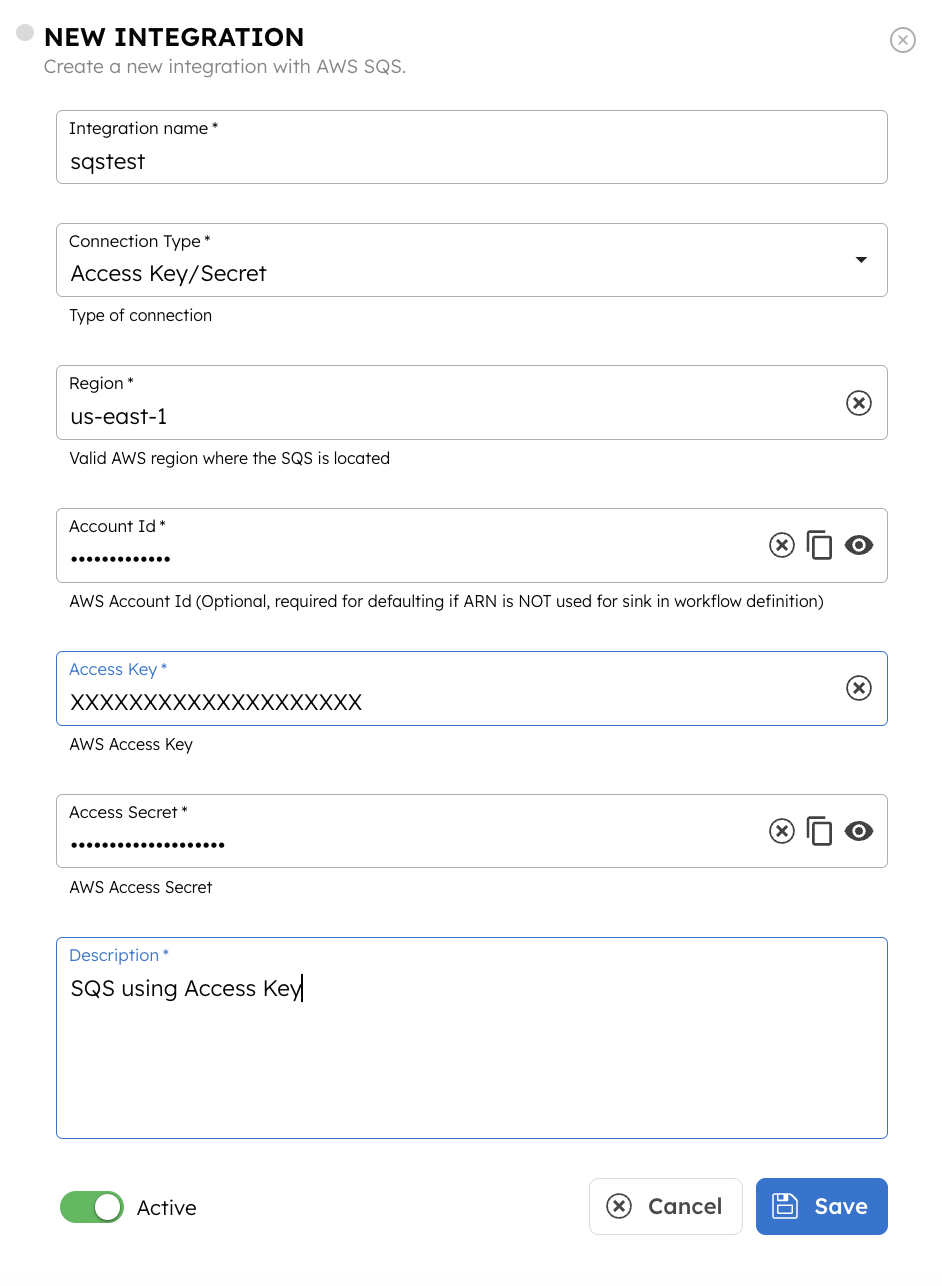
- (Optional) Toggle the Active button off if you don’t want to activate the integration instantly.
- Select Save.
Step 3: Set access limits to integration
Once the integration is configured, set access controls to manage which applications or groups can use the message broker.
To provide access to an application or group:
- Go to Access Control > Applications or Groups from the left navigation menu on your Conductor cluster.
- Create a new group/application or select an existing one.
- In the Permissions section, select + Add Permission.
- In the Integration tab, select the required message broker and toggle the necessary permissions.
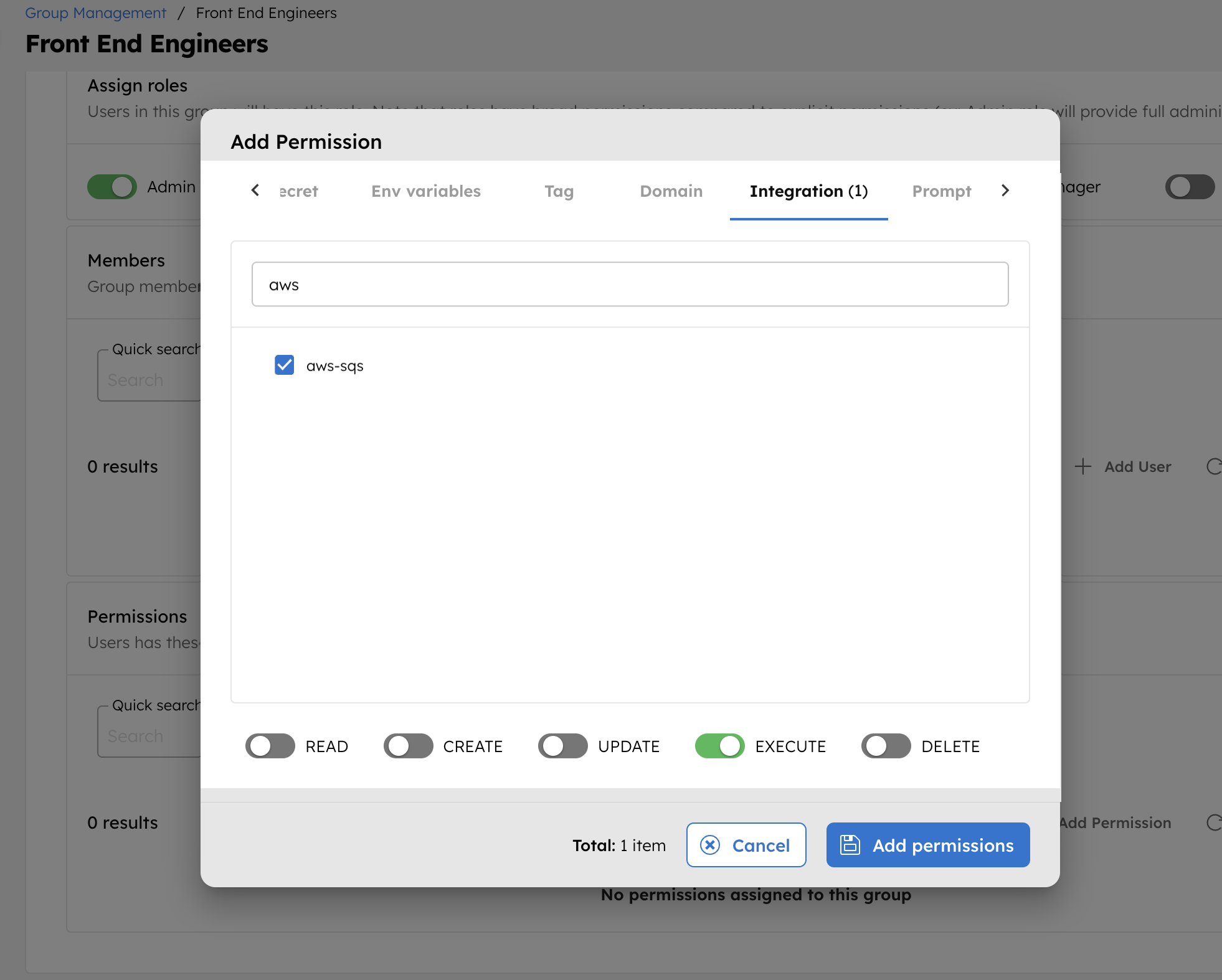
The group or application can now access the message broker according to the configured permissions.
Next steps
With the integration in place, you can now:
- Create Event Handlers.
- Configure Event tasks.
- Enable Change Data Capture (CDC) to send workflow state changes to message brokers.